第1题:
第2题:
第3题:
The reason why lesson six skips the puzzle questions is that they are associated with the expertise based on the content of a particular subject which is likely irrelevant to a layman.()
第4题:
By default, which of the following factors determines the spanning-tree path cost?()
第5题:
第6题:
第7题:
第8题:
Questions 59-60 are based on the following information
A hash table With hash function
H1(k)=k mod 13
Is shown below.
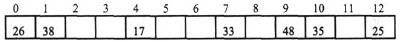
Collision is resolved using the hash function H2(k)=(k mod 11)+1
How many key comparisons occur in searching for key 35 in the given hash table?
A.0
B.1
C.2
D.3
第9题:
第10题:
Which of the following devices can be installed on individual computers throughout the network?()